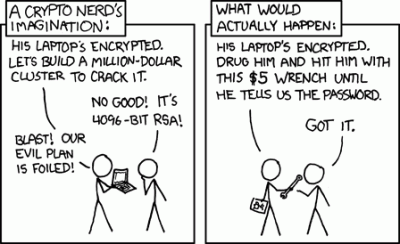
Updates (September 12, 2013):
Since this post was published, more information has become clear. First, this MacWorld article has details about the Touch ID fingerprint reader. It’s very interesting.
Second, Apple pulled the iCloud Keychain feature from iOS 7 GM. This makes Touch ID a lot less useful. It looks like access to Touch ID is also not yet allowed for third party apps. This is a shame. My guess is that these two things have been delayed, not cancelled. Perhaps iOS 7.1 released alongside OS X Mavericks, which still lists iCloud Keychain as a feature?
Security vs Convenience
There is always a battle between security and convenience. Not only when it comes to technology, but in every aspect of our lives. Otherwise we wouldn’t have locks in our house doors that force us to carry keys everywhere.
When it comes to personal computing, the importance of security has increased exponentially. Smartphones are computers that have lots of personal data and that we carry with us everywhere. Contacts, email, apps with financial info, photographs of our family with embedded GPS coordinates… Someone with malicious intent can do a lot of damage if they get to your phone.
Not only do we carry all this with us, but we keep a lot of personal information online. Some websites may be good about safeguarding it. But many aren’t. Stolen databases are scarily common.
To make things worse, most people re-use the same password (or a few of them) everywhere. And to make things even worse, computer power and sophisticated tools for brute-force cracking of passwords are more effective than you would think, especially if you aren’t using particularly strong passwords.
Why do we do this? It’s the battle. We have limited human memories, and typing strong passwords on a phone is a pain in the ass. Tools like 1Password (I’m a big fan) are very helpful but they still add a layer of inconvenience to the user experience.
Fixing the security issue while adding convenience
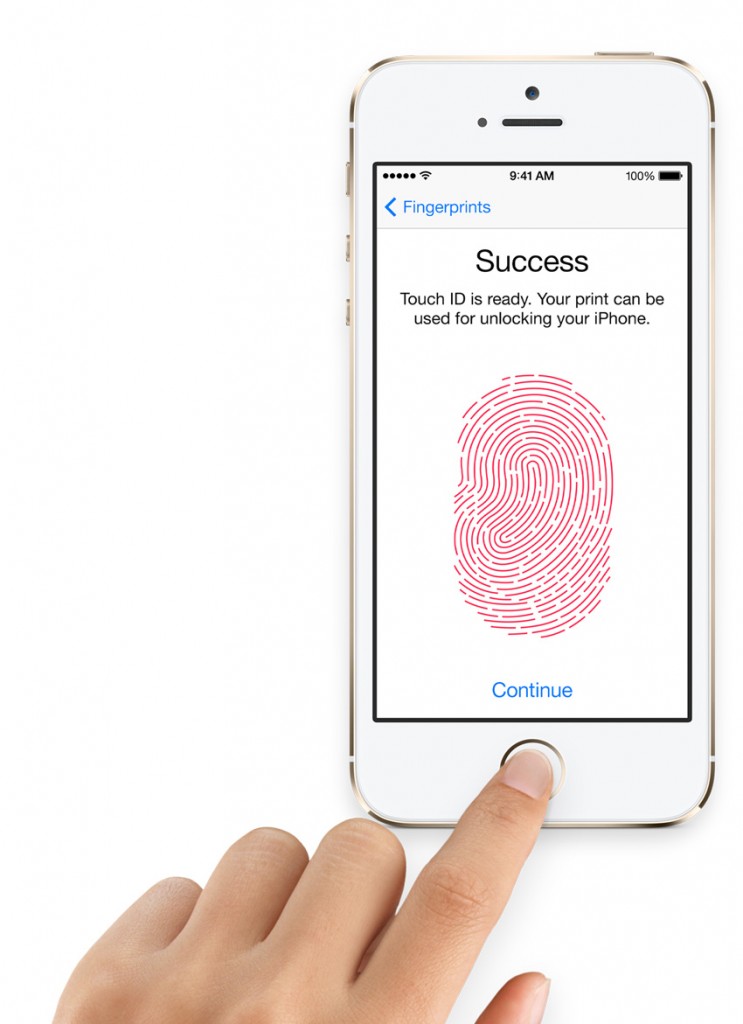
Touch ID is a new fingerprint sensor that lives inside the home button of the iPhone 5s. Someone who doesn’t understand security may think it’s boring. But this both improves security (put your finger on the button, the software fills in a unique strong password for you) and removes inconvenience.
Other iPhone 5s features are important but incremental improvements: better camera, faster processor… this one is a leap in functionality. It’s a solution to one of the most annoying usability aspects of smartphones: typing passwords at all times. And it’s a solution to the most glaring problem with most user’s security: reusing weak passwords.
Why wasn’t it done before
Surely you’ve seen Lenovo or Dell laptops with fingerprint readers. Why didn’t anyone slap one on a phone before?
Because they sucked. They are large, slow, require a swipe, in a specific direction and are inaccurate. I don’t know of anyone who uses his other than when mandated by work. Just read this.
Now see the video about Touch ID.
All these technical challenges had to be solved in order to embed a fingerprint sensor into the iPhone 5s. There is a special new sensor, a sapphire crystal button, special co-processor hardware in the A7 chip for storing and decoding fingerprints, and code in the operating system to integrate the functionality. No other company could pull something like this off. Not Google, not Microsoft, not Samsung.